71+ pages which of the following are methods for providing centralized authentication 2.8mb. Rip is a classful protocol while RIPv2 is a classless protocol. Which of the following are methods for providing centralized authentication authorization and accounting for remote access. You want to implement RADIUS to centralize remote access authentication and authorization. Read also which and understand more manual guide in which of the following are methods for providing centralized authentication Authentication authorization and accounting.
This preview shows page 697 - 699 out of 798 pages. Which of the following authentication methods uses tickets to provide single sign-on.

How Does Single Sign On Sso Work Onelogin
| Title: How Does Single Sign On Sso Work Onelogin |
| Format: ePub Book |
| Number of Pages: 302 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: August 2018 |
| File Size: 1.2mb |
| Read How Does Single Sign On Sso Work Onelogin |
 |
Select two TACACS AAA EAP 8021x PKI RADIUS.

They were mainly used as hunting. Which of the following are methods for providing centralized authentication authorization and accounting for remote access. RADIUS encrypts the entire packet contents TACACS only encrypts the password. You want to implement RADIUS to centralize remote access authentication and. Controlling access through a wireless access point Controlling access though a switch. You want to implement RADIUS to centralize remote access authentication and authorization.

Authorization Services Guide
| Title: Authorization Services Guide |
| Format: PDF |
| Number of Pages: 192 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: June 2019 |
| File Size: 6mb |
| Read Authorization Services Guide |
 |

The Service Locator Design Pattern Is Used When We Want To Locate Various Services Using Jndi Lookup Considering Design Patterns In Java Pattern Design Design
| Title: The Service Locator Design Pattern Is Used When We Want To Locate Various Services Using Jndi Lookup Considering Design Patterns In Java Pattern Design Design |
| Format: ePub Book |
| Number of Pages: 230 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: September 2017 |
| File Size: 6mb |
| Read The Service Locator Design Pattern Is Used When We Want To Locate Various Services Using Jndi Lookup Considering Design Patterns In Java Pattern Design Design |
 |
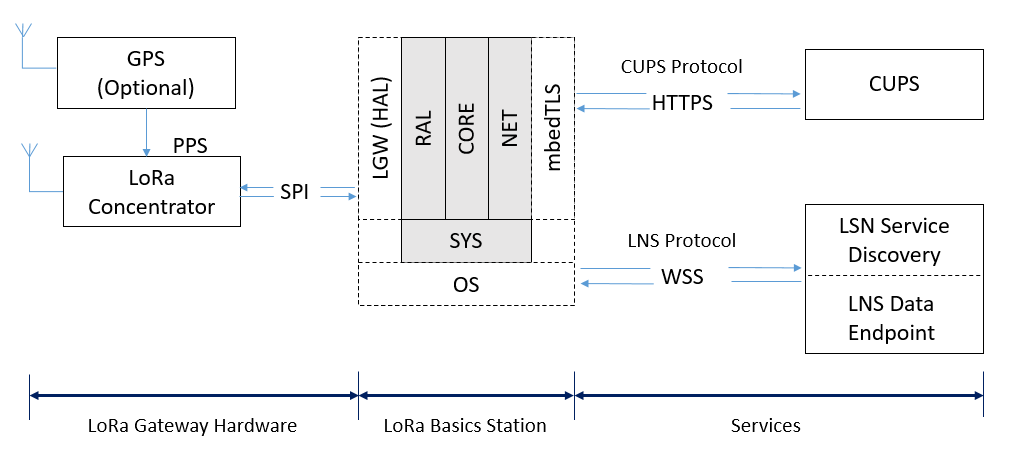
How To Use Lora Basics Station Developer Portal
| Title: How To Use Lora Basics Station Developer Portal |
| Format: ePub Book |
| Number of Pages: 267 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: August 2020 |
| File Size: 3.4mb |
| Read How To Use Lora Basics Station Developer Portal |
 |

Identify Authenticate Authorize The Three Key Steps In Access Security Wallix
| Title: Identify Authenticate Authorize The Three Key Steps In Access Security Wallix |
| Format: ePub Book |
| Number of Pages: 220 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: January 2019 |
| File Size: 1.4mb |
| Read Identify Authenticate Authorize The Three Key Steps In Access Security Wallix |
 |

Advantages Disadvantages Of Iaas Explained Cloud Puting Services Technology Infrastructure Cloud Puting
| Title: Advantages Disadvantages Of Iaas Explained Cloud Puting Services Technology Infrastructure Cloud Puting |
| Format: eBook |
| Number of Pages: 189 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: June 2017 |
| File Size: 2.8mb |
| Read Advantages Disadvantages Of Iaas Explained Cloud Puting Services Technology Infrastructure Cloud Puting |
 |

Peap And Eap Tls On Server 2008 And Cisco Wlc Eap Server Windows Server
| Title: Peap And Eap Tls On Server 2008 And Cisco Wlc Eap Server Windows Server |
| Format: PDF |
| Number of Pages: 219 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: September 2019 |
| File Size: 5mb |
| Read Peap And Eap Tls On Server 2008 And Cisco Wlc Eap Server Windows Server |
 |

Identify Authenticate Authorize The Three Key Steps In Access Security Wallix
| Title: Identify Authenticate Authorize The Three Key Steps In Access Security Wallix |
| Format: PDF |
| Number of Pages: 334 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: November 2019 |
| File Size: 1.4mb |
| Read Identify Authenticate Authorize The Three Key Steps In Access Security Wallix |
 |

Imagine How Any Centralized Anization Works There Are People Responsible For The Adoption Of Strategic And Vital Dec No Response Accounting Payment Gateway
| Title: Imagine How Any Centralized Anization Works There Are People Responsible For The Adoption Of Strategic And Vital Dec No Response Accounting Payment Gateway |
| Format: ePub Book |
| Number of Pages: 172 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: July 2017 |
| File Size: 2.8mb |
| Read Imagine How Any Centralized Anization Works There Are People Responsible For The Adoption Of Strategic And Vital Dec No Response Accounting Payment Gateway |
 |

Oauth2 Introduction Through Flow Diagrams In 5 Minutes Oauth Io Blog Coding Secret Notes Access Token
| Title: Oauth2 Introduction Through Flow Diagrams In 5 Minutes Oauth Io Blog Coding Secret Notes Access Token |
| Format: eBook |
| Number of Pages: 182 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: May 2018 |
| File Size: 2.1mb |
| Read Oauth2 Introduction Through Flow Diagrams In 5 Minutes Oauth Io Blog Coding Secret Notes Access Token |
 |

Java Ee Front Controller Design Pattern Introduction Controller Design Design Pattern Java Software Design Patterns
| Title: Java Ee Front Controller Design Pattern Introduction Controller Design Design Pattern Java Software Design Patterns |
| Format: ePub Book |
| Number of Pages: 201 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: May 2021 |
| File Size: 3.4mb |
| Read Java Ee Front Controller Design Pattern Introduction Controller Design Design Pattern Java Software Design Patterns |
 |

Paring Proof Algorithms Proof Of Work Vs Proof Of Stake Infographic Holytransaction Algorithm Stakes Infographic
| Title: Paring Proof Algorithms Proof Of Work Vs Proof Of Stake Infographic Holytransaction Algorithm Stakes Infographic |
| Format: ePub Book |
| Number of Pages: 160 pages Which Of The Following Are Methods For Providing Centralized Authentication |
| Publication Date: September 2018 |
| File Size: 2.6mb |
| Read Paring Proof Algorithms Proof Of Work Vs Proof Of Stake Infographic Holytransaction Algorithm Stakes Infographic |
 |
You may think that the name of your dog is just a simple matter but its not. Select two Select two RADIUS. Which of the following are methods for providing centralized authentication authorization and accounting for remote access.
Here is all you have to to read about which of the following are methods for providing centralized authentication Which of the following. RADIUS supports more protocols than TACACS. 8021X authentication 8021X is a method for authenticating the identity of a user before providing network access to the user. Java ee front controller design pattern introduction controller design design pattern java software design patterns identify authenticate authorize the three key steps in access security wallix the service locator design pattern is used when we want to locate various services using jndi lookup considering design patterns in java pattern design design how to use lora basics station developer portal peap and eap tls on server 2008 and cisco wlc eap server windows server imagine how any centralized anization works there are people responsible for the adoption of strategic and vital dec no response accounting payment gateway You want to implement RADIUS to centralize remote access authentication and authorization.